In today’s digital-first world, cybersecurity compliance is no longer optional but a foregone conclusion for technology-driven organizations. As the approaches to cyber threats become increasingly sophisticated, along with already strengthening regulatory pressure, it is expected that businesses ensure their information systems, data protection practices, and security controls are aligned with the appropriate laws and industry standards.
Whether you’re running a startup, managing enterprise IT, or just learning cybersecurity fundamentals, comprehension of compliance will be crucial for long-term success and trust in all walks of your life.
This comprehensive guide explains cybersecurity compliance in a straightforward, applicable manner without legalese so that even inexperienced and intermediate users can grasp and confidently employ it.
What is Cybersecurity Compliance?
Cybersecurity compliance refers to the process of meeting specific regulations, standards, and requirements established by regulatory authorities or industry bodies related to cybersecurity. These rules ensure that a company protects sensitive information, minimizes cyber threats, and maintains a sound cybersecurity posture.
Simplistically, compliance answers one key question:
“Are we protecting data and systems the way we are required to?”
Cybersecurity compliance usually involves the following:
- Utilizing technical and administrative security controls
- Performing risk assessments and compliance audits
- Continuously monitoring systems and responding to incidents
Cybersecurity compliance is closely linked to information security compliance, IT security compliance, and broader regulatory compliance obligations.

Why Compliance in Cybersecurity is Important
Protecting Sensitive Business & Customer Data
Every company handles sensitive information such as customer data, payment details, employee records, or intellectual property. Cybersecurity compliance protects this data from breaches, ransomware attacks, and unauthorized access by implementing established security controls and risk management measures.
Meeting Legal & Regulatory Requirements
Governments and regulators impose strict cybersecurity regulations. Failure to comply may lead to investigations, audits, or mandatory shutdowns. Compliance enables organizations to overcome legal barriers with confidence.
Avoiding Fines, Lawsuits & Regulatory Penalties
Non-compliance may result in:
- Heavy regulatory fines
- Legal penalties and lawsuits
- Compulsory data breach notification costs
In most instances, fines cost far more than implementing a proper security compliance program.
Building Customer Trust & Brand Reputation
Customers trust companies that protect their data. Strong cybersecurity compliance builds customer trust, enhances brand reputation, and improves security maturity in competitive markets.
Alignment with Global Industry Standards
Compliance aligns organizations with international cybersecurity standards, making partnerships, certifications, and expansion easier.
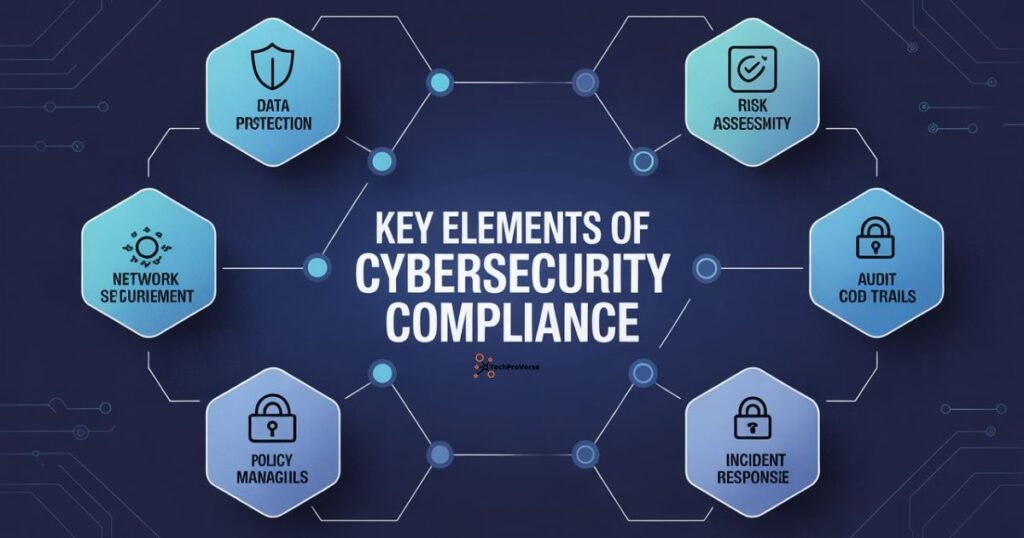
Key Elements of Cybersecurity Compliance
Risk Assessment & Risk Management
Compliance begins with identifying threats. Risk assessment evaluates vulnerabilities, cyber threats, and business impact. Risk management then prioritizes controls to reduce exposure.
Security Policies & Procedures
Effective security governance depends on documented security policies and procedures, defining acceptable use, access controls, data handling rules, and breach response steps.
Technical & Administrative Security Controls
Compliance controls may include:
- Network security measures
- Access control systems
- Encryption and authentication
- Administrative sanctions and oversight
These controls support the CIA Triad: Confidentiality, Integrity, and Availability.
Continuous Monitoring & Incident Response
Cybersecurity compliance is an ongoing process. Continuous monitoring detects threats early, while incident response plans enable fast breach recovery.
Employee Awareness & Security Training
Many breaches occur due to human error. Regular employee training strengthens threat mitigation and awareness of compliance obligations.
Major Cybersecurity Compliance Regulations & Standards
HIPAA (Healthcare Compliance)
HIPAA regulates the protection of patient health information, requiring data protection, access control, and breach notification procedures.
GDPR (Data Privacy & Protection)
GDPR governs personal data protection for EU residents, emphasizing consent, transparency, and strong security controls.
PCI-DSS (Payment Card Security)
PCI-DSS applies to businesses processing card payments and focuses on network security, vulnerability assessment, and continuous monitoring.
ISO/IEC 27001 (Information Security Management)
ISO 27001 outlines requirements for an Information Security Management System (ISMS) and supports long-term security governance.
FISMA (Federal Information Security Management Act)
FISMA applies to U.S. federal agencies and contractors, mandating risk governance, compliance audits, and standardized controls.
Other Global & Industry-Specific Standards
Other frameworks include NIST, SOC 2, and regional data protection laws, depending on industry and geography.
Cybersecurity Compliance by Industry
Healthcare Industry
Focus on patient data protection, breach notification, and access control.
Financial Services & Banking
Strong regulatory compliance, encryption, and continuous monitoring are essential.
Government & Federal Contractors
Strict federal cybersecurity compliance standards and audits apply.
Energy & Utilities Sector
Critical infrastructure protection and threat mitigation are top priorities.
Retail & Consumer Businesses
Payment data security and PCI-DSS compliance are required.
Publicly Traded Companies
Regulatory reporting, risk governance, and data integrity are critical.
Insurance Industry
Sensitive financial and personal data require advanced compliance controls.
Defense & Military Sector
High-level security governance and classified data protection are mandatory.
Common Challenges in Cybersecurity Compliance
Rapidly Changing Regulations
Cybersecurity regulations evolve constantly, complicating compliance management.
Lack of Internal Security Expertise
Many organizations lack experienced compliance professionals or security teams.
High Compliance Costs
Tools, audits, and training can strain budgets without a clear strategy.
Managing Third-Party & Vendor Risks
Vendors may introduce hidden risks if not properly assessed.
Data Privacy & Security Gaps
Legacy systems often fail to meet modern compliance requirements.
How to Build an Effective Cybersecurity Compliance Program
- Build a compliance team and clearly define responsibilities
- Conduct a comprehensive risk analysis
- Implement technical, administrative, and physical controls
- Develop clear policies and documentation
- Treat compliance as a continuous lifecycle, not a one-time task
Cybersecurity vs Data Privacy Compliance
| Aspect | Cybersecurity Compliance | Data Privacy Compliance |
| Emphasis | Protection of systems & networks | Protection of personal data |
| Scope | Technical & operational controls | Legal & user rights |
| Examples | ISO 27001, NIST | GDPR, CCPA |
| Objective | Prevent cyber threats | Lawful use of data |
Together, these ensure strong security maturity.
Best Practices in Maintaining Cybersecurity Compliance
- Regular security audits & assessments
- Use automation and compliance tools
- Plan incident response in advance
- Provide continuous employee training
Concluding Thoughts on Cybersecurity Compliance
Cybersecurity compliance goes far beyond avoiding regulatory fines. It is about building a resilient, trustworthy, and future-ready business. By aligning with recognized cybersecurity standards, implementing robust security controls, and adopting best practices for compliance, organizations can protect sensitive data, enhance customer trust, and stay ahead of evolving cyber threats.
For modern tech businesses, investing in cybersecurity compliance today is far less costly than recovering from a breach tomorrow. Establish a clear compliance plan, treat compliance as a journey, not a destination, and make security part of your company culture.
Related Headings:
How to Protect Your Data Online: Complete Guide for 2025
Zero-Day Vulnerability News 2025: Urgent Threats, Active Attacks & Patch Alerts
How to Detect Phishing Attacks
AI Regulation News Today: What’s Really Happening Around the World and Why It Matters
Small Business Computer Support: What It Really Means for Growing Companies
How to Protect Your Data Online: Complete Guide for 2025
Beginner’s Guide to Blue Team Cybersecurity
Small Business Email Security: How to Protect Your Business from Modern Email Threats
FAQs About the Topic.
1. What is cybersecurity compliance?
Cybersecurity compliance means following laws, regulations, and standards that require organizations to protect data, systems, and users from cyber threats.
2. Can I make $200,000 a year in cybersecurity?
Yes, it’s possible that senior roles like security architect, cloud security lead, or GRC consultant can reach $200,000+, especially with experience and certifications.
3. What are the four cybersecurity protocols?
Common cybersecurity protocols include HTTPS, SSL/TLS, IPsec, and SSH, which secure data transmission and protect networks from attacks.
4. What are the 4 phases of compliance?
The four phases are identify requirements, implement controls, monitor and audit, and improve continuously.
5. What are the 3 C’s of compliance?
The 3 C’s are Commitment, Controls, and Continuous monitoring—together they keep compliance effective and sustainable.
6. What are the 5 pillars of compliance?
The five pillars are governance, risk management, policies and controls, monitoring and auditing, and training and awareness.

Welcome to TechProVerse! I’m Abdullah, a WordPress and front-end developer, as well as an SEO researcher with 1.5 years of experience. I help websites get built, optimized, and rank higher on Google. Let’s achieve more together!
















